ArmorAML® complies with the provisions of the LFPIORPI Law, CNBV, UIF, and international FATF standards.

Contact Us
Enter your details in the form and we will contact you shortly.
ArmorAML® The compliance technology chosen by:






























Why ArmorAML®?
It is a comprehensive platform that simplifies, automates, and strengthens Anti-Money Laundering processes. Thanks to its specialized modules, automated reports, and Risk-Based Approach, it allows organizations to comply with regulations, minimize sanction risks, and respond with agility to audits.
Choosing ArmorAML® means opting for a solution designed to comply with the provisions of the LFPIORPI, CNBV, UIF, and international FATF standards.
CNBV Technical Compliance
Infrastructure audited to comply with the strict information security annexes required by the authority.
Data Centralization
We unify dispersed data sources (Transactional, KYC, KYE) into a single coherent structure, facilitating Business Intelligence (BI) and auditing.
Secure & Encrypted Architecture
Total information protection using advanced encryption in transit and at rest, under ISO/IEC 27001 certification.
System Interconnection
We advise your IT team to define the necessary protocols that guarantee interoperability between ArmorAML and your current infrastructure.
We are certified in ISO/IEC 27001:2022

We operate under an Information Security Management System with controls integrated across three key areas of our operation.
Design and Development:
Architecture, programming, and code assurance processes aligned with formal security controls and the protection of critical information.
Implementation:
Secure deployment of solutions, configuration management, and access controls applied under a structured information security approach.
Support and Maintenance:
Operational continuity, monitoring, incident management, and controlled updates that strengthen the stability and security of our platforms.
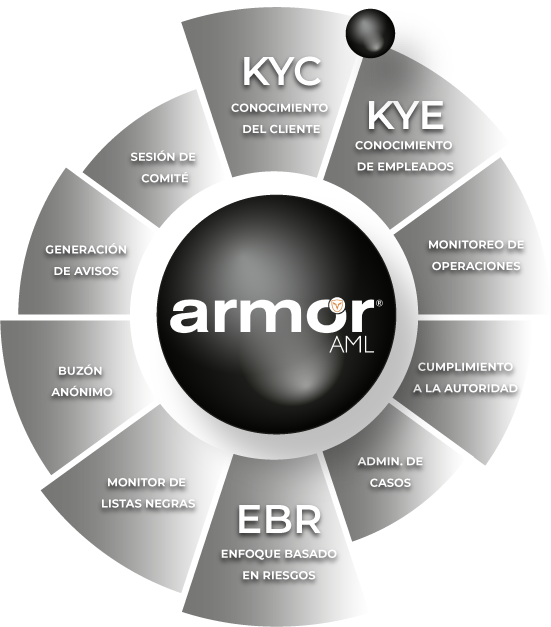
How does our comprehensive anti-money laundering solution work? Meet the pillars of our Intelligent Compliance architecture.
Risk-Based Approach (RBA)
Generates the Entity Risk Assessment and assigns specific risk levels to clients through a configurable dynamic risk matrix, ensuring alignment with your internal methodology.
Client Risk Assessment Model
Our scoring model automates risk grading to guarantee a precise, objective, and auditable Risk-Based Approach (RBA), eliminating subjective bias in client classification.
Watchlist Screening Engine
Manages internal blocklists and unifies regulatory or third-party lists (PEPs, OFAC, UN, 69-B), ensuring a robust screening engine fully aligned with the regulatory framework.
Regulatory Reporting
Automatically generates reports for the authority based on required layouts, strictly aligned with local regulations and standards, ensuring error-free submissions.
Alert Generation
Triggers regulatory alerts based on official identification and reporting thresholds. Custom alerts can also be configured to match the entity’s specific internal policies.
Case Management
A centralized hub to manage alerts, visualize client profiles, conduct investigations, and digitally store evidence, creating a complete Audit Trail for every decision.
Transaction Monitoring
Continuously monitors client transactions to detect patterns and generate alerts based on regulatory parameters or behavioral anomalies (unusual transactional profiles).
Whistleblowing Channel
Enables the anonymous reporting of suspicious internal conduct by employees or officials. Each report automatically creates a case for formal investigation.
ArmorAML - Comprehensive Anti-Money Laundering Solution
Designed for real-time interoperability. ArmorAML® adapts to your institution’s technological maturity, allowing integrations via Real-Time API or high-volume Batch processing, without forcing you to modify your current Core Banking system.
API RESTful (JSON)
Synchronous connection for critical validations in under 1 second. Ideal for digital Onboarding processes and immediate watchlist screening directly from your web or mobile application.

Real-Time Interoperability
Microservices Architecture: «Our architecture allows for identity verification and watchlist screening with sub-second latency.
Universal Standards: We utilize RESTful standards and JSON format to ensure lightweight and universal communication between your Front-end and our Risk Engine.
Automated Ingestion: Eliminates manual input: data ingestion is automated and validated at the source.
Data Integration Methods
ArmorAML®, in addition to API connectivity, facilitates data incorporation—if business operations preclude real-time transmission—through two alternative integration interfaces:

Flat File Load (TXT/Excel)
Agile processing of standard layouts. We enable manual or automated data ingestion via flat files (TXT) and spreadsheets (Excel/CSV), facilitating historical data migration or operational batch loads without complex development.
Staging Tables
Direct integration at the database level. We enable intermediate tables for the massive exchange of transactional and client data, optimizing performance within high-volume infrastructures.
